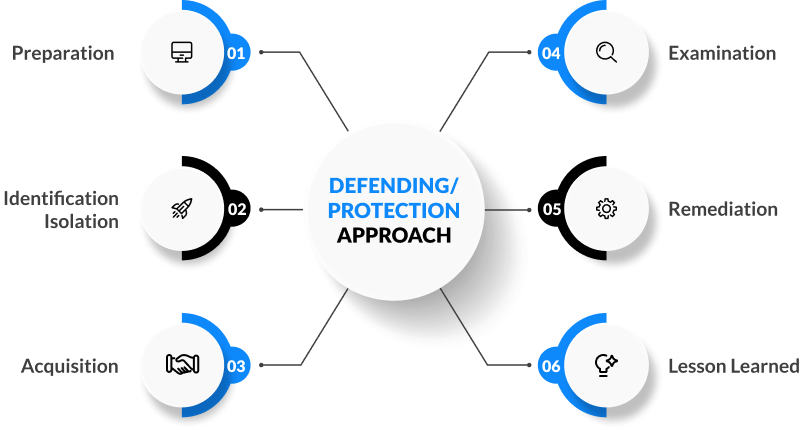
Wateen greatly emphasizes cybersecurity, utilizing the NIST Cybersecurity Framework’s core components – Identify, Protect, Detect, Respond, and Recover. This approach is essential in safeguarding their systems against cyber threats. The flexibility of the NIST framework allows Wateen to customize it to their specific security needs, enhancing their existing cybersecurity processes and aligning with industry standards.
As an ICT/Managed Security Services/Integrated Services provider, Wateen acknowledges the NIST Cybersecurity Framework’s reputation as a top method for managing cybersecurity risks. By adopting this framework, Wateen aims to bolster its cybersecurity stance and maintain the trust of its customers.
In essence, the NIST Cybersecurity Framework is central to Wateen’s commitment to upholding the highest standards in cybersecurity. Their implementation of this framework demonstrates a continuous effort to improve their cybersecurity resilience and protect their clients’ valuable information.

Devices
- Identify: EDR
- Proctect: EDR
- Detect: EDR & SIEM
- Respond: SOAR & MDR Service
- Recover: SOAR & MDR Service

Applications
- Identify: VA
- Proctect: IR Services
- Detect: PT & IR Services
- Respond: SOAR & IR Service
- Recover: SOAR & IR Service

Networks
- Identify: VA
- Proctect: XDR
- Detect: SIEM & IR Services
- Respond: SOAR & IR Service
- Recover: SOAR & IR Service

Data
- Identify: DLP & SIEM
- Proctect: DLP
- Detect: DLP & IR Services
- Respond: DLP, SOAR & IR Service
- Recover: DLP, SOAR & IR Service

Users
- Identify: EDR
- Proctect: EDR
- Detect: EDR & SIEM
- Respond: SOAR & MDR Service
- Recover: SOAR & MDR Service

Major Capabilities
- Incident Response & Recovery
- Threat Intelligence
- Defense In Depth
- Endpoint Security
- Compliance Management
- Security Expertise
- IT Audits
- Trainings
Technology Solutions
- Endpoint Detection & Response (EDR)
- Extended Detection and Response (XDR)
- Security Information & Event Management (SIEM)
- Security Orchestration, Automation, & Response (SOAR)
- Multi Factor Authentication (MFA)
- Data Loss Prevention (DLP)
- Data Classification
- Email/Web Gateway
- Digital Risk Intelligence







